20+ perimeter network diagram
In this Figure ACL of a router R3 is modified to reject any IP. The example of the network diagram below shows network architecture with configuration called two firewall demilitarized zone.

Managed Security Solution Brief Masergy
Use Createlys easy online diagram editor to edit this diagram collaborate with others and export results to multiple image formats.
. Review the existing perimeter network and identify problems. Perimeter Network Design 9 Chapter 10 449 Designing VPN and Remote Access Termination Networks A VPN or remote access termination network is a perimeter network. This could be done in a back-to-back configuration two firewalls surrounding the DMZ as shown in Figure 8-2 or as a 3-leg perimeter configuration.
Perimeter Network Layoutsgif. 12 what are the differences between the perimeter. A network diagram is a way to illustrate the relationships among components.
Critical points within the CDE The perimeter of the CDE Change management. Perimeter Network Exchange Server Diagram give our company a lot of each. Designing security of wireless network implementations integration with overall network design technical design for a secure perimeter network overall architecture types and functions of.
11 and will be the network design that is referenced throughout this chapter. This paper implements and evaluates the performance of a network fundamental diagram NFD proportional-integral perimeter controller PC using base tuned parameters. School University of South Florida.
Certain you probably recognized that having the capacity to reservoir publications online. Figure 12 illustrates the internal network separated by router R3 for stations DB User 4 as the attacker and HTTP User 1and 2. Secure internal services outside your VPNperimeter network during a zero-trust transition.
Download scientific diagram GPSRs Perimeter Strategy from 20 from publication. BeyondCorp-inspired HTTPSSSO Access Proxy. When drawing a network diagram youll need three things.
Demilitarized zone DMZ is a host or network segment. State Diagram Camera Sensor. Symbols representing those components.
In this sample network design the Internet cloud is shown in the upper. Parametric Diagram for Link. Network Diagram Two Parts to the Analysis Forward Pass Calculates the Duration of the Project Backward Pass Calculates the slackfloat for each task and shows the critical path.
In network security a screened subnet refers to the use of one or more logical screening routers as a firewall to define three separate subnets. Unicast Ad-Hoc Routing in Vehicular City Scenarios ResearchGate the professional network for scientists. Designing security of wireless network implementations integration with overall network design technical design for a secure perimeter network overall architecture types and functions of.
The traditional design uses. Thus the total number of parameters in a feed-forward neural network with one hidden layer is given by. Open the following files which are located in the dc1tools folder.
Using a project network diagram and agile framework can help you predict upcoming issues so you can immediately decide if you need more or less time in a single task. In the previous diagram there are two architectures given. A network diagram is shown in Figure.
I h h o h o Since this network is a small network it was also. 12 What are the differences between the perimeter network and the interior. Often called a De-Militarized Zone DMZ it is a buffer between attackers and your internal network.
Mapping of DDoS mitigation components to attack types Cloud-based DDoS scrubbing service A cloud-based DDoS scrubbing service is a critical component of any. An external router sometimes called an access. Network data flow diagrams will help optimize network testing by identifying connections at.
Block Diagram for Sensor Network. Course Title ISM 6328.
A Bird S Eye View Of A Typical Lm Download Scientific Diagram
2

Extending The Zero Trust Architecture Concept To Apis Vmware Security Blog Vmware

What Is Zero Trust Vmware Security Blog Vmware
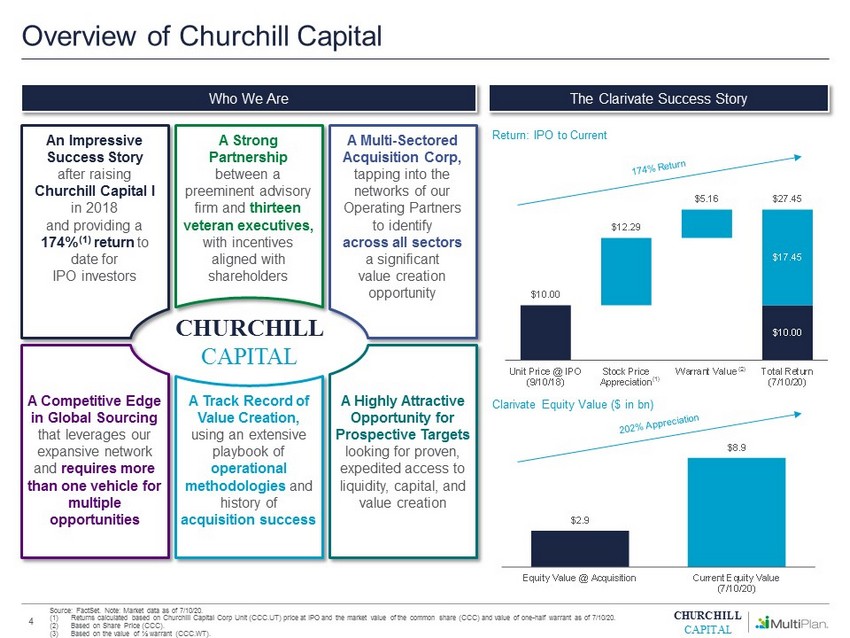
Ex99x2 004 Jpg

U S Security Agencies Release Network Security Vulnerability Guidance Esecurityplanet
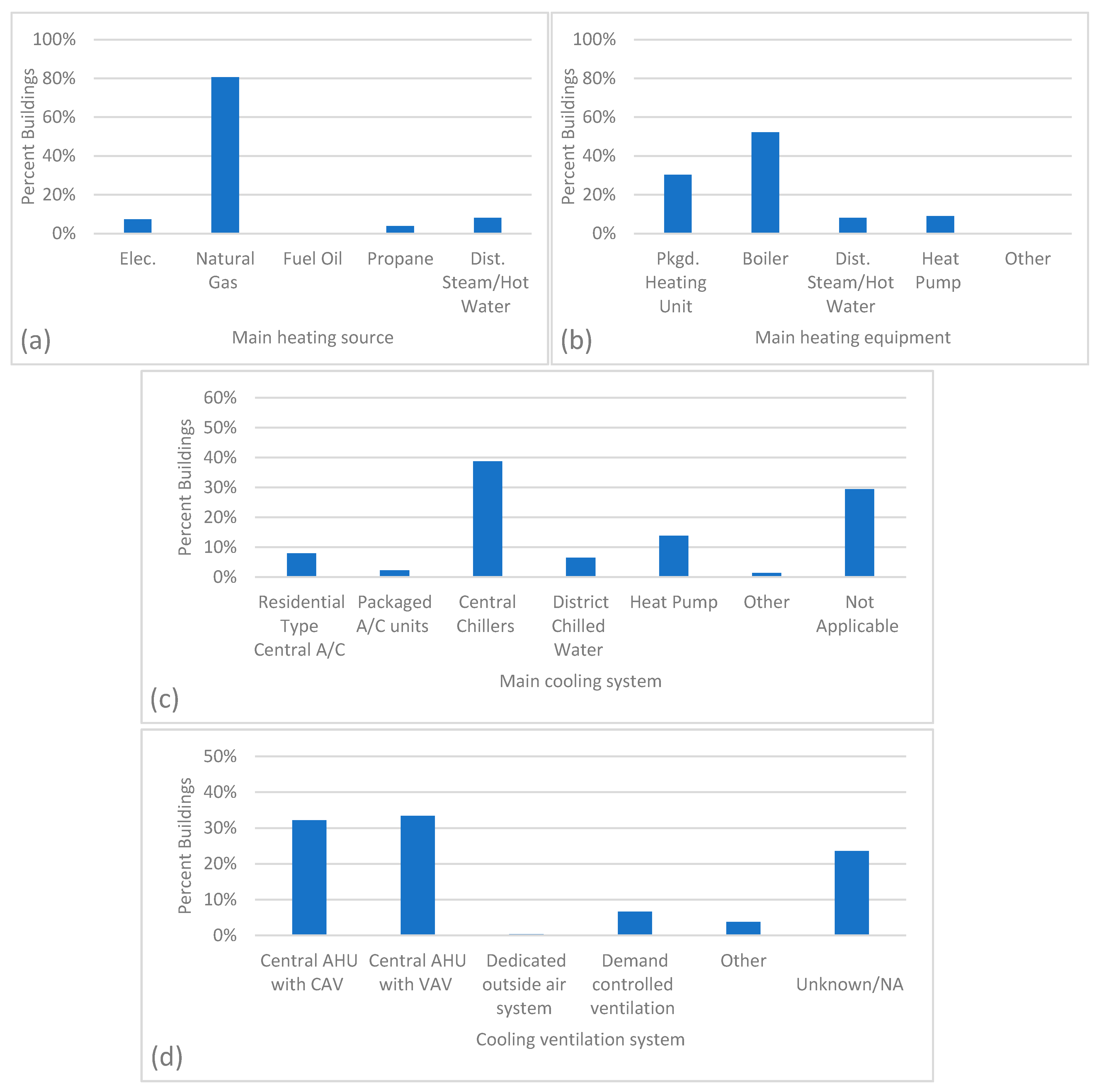
Energies Free Full Text A Process For Defining Prototype Building Models Courthouse Case Study For U S Commercial Energy Html

Networking For Secure Intra Cloud Access Reference Architectures Cloud Architecture Center Google Cloud
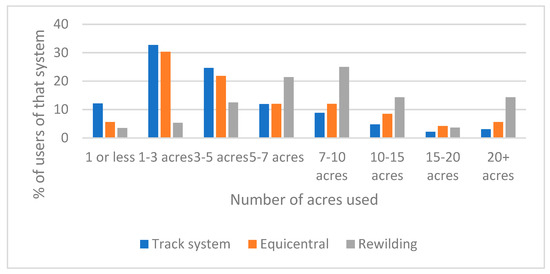
Animals Free Full Text An Exploration Of Environmentally Sustainable Practices Associated With Alternative Grazing Management System Use For Horses Ponies Donkeys And Mules In The Uk Html

What Is Zero Trust Vmware Security Blog Vmware
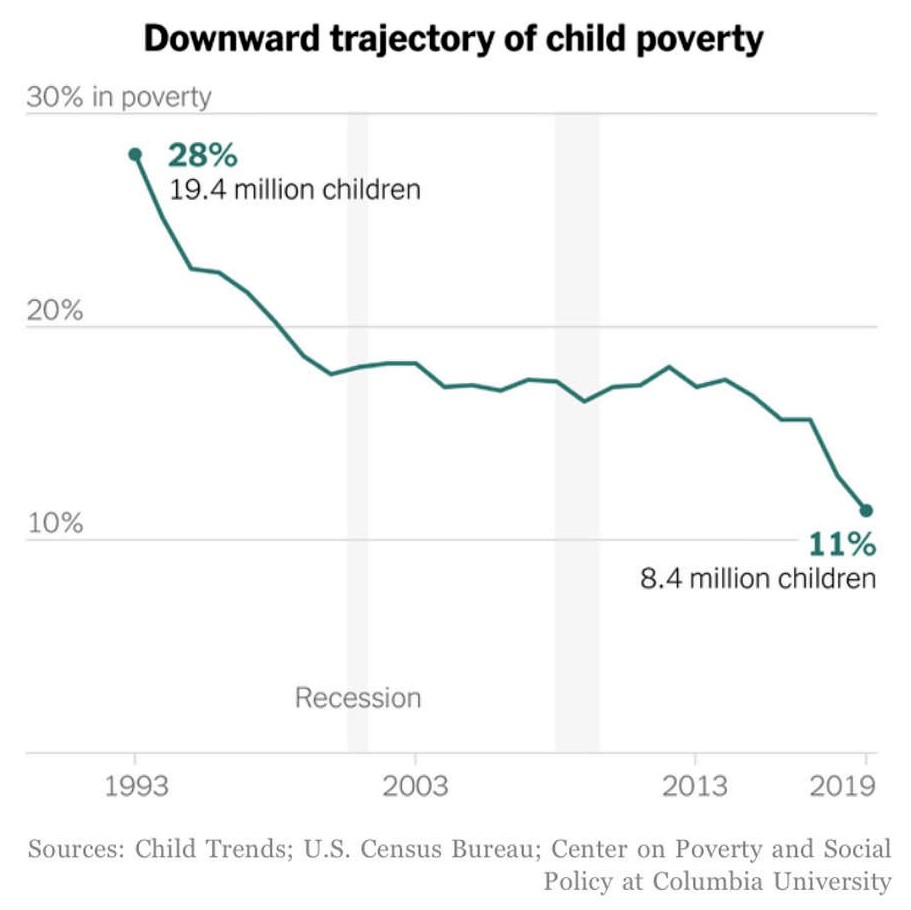
Yvgz7axii8j9vm

What Is Zero Trust Vmware Security Blog Vmware

Best Practices Noise
A Rectangle Has The Sum Of Length And Breadth 20cm What Is The Perimeter Quora

Threat Intelligence Apps Integrations Plugins Crowdstrike Store
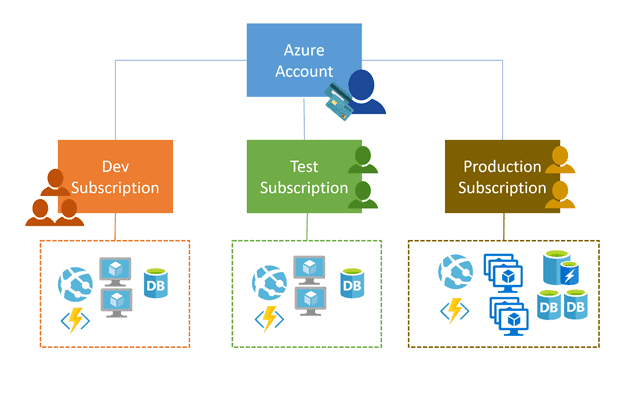
Azure Azure Fundamentals Day 1 Training Az 900

Security And Networking Blog Cato Networks